Data privacy notice Flowchart australian goverment published possolutions Security event logging, why it is so important – aykira internet solutions data privacy process flow diagram
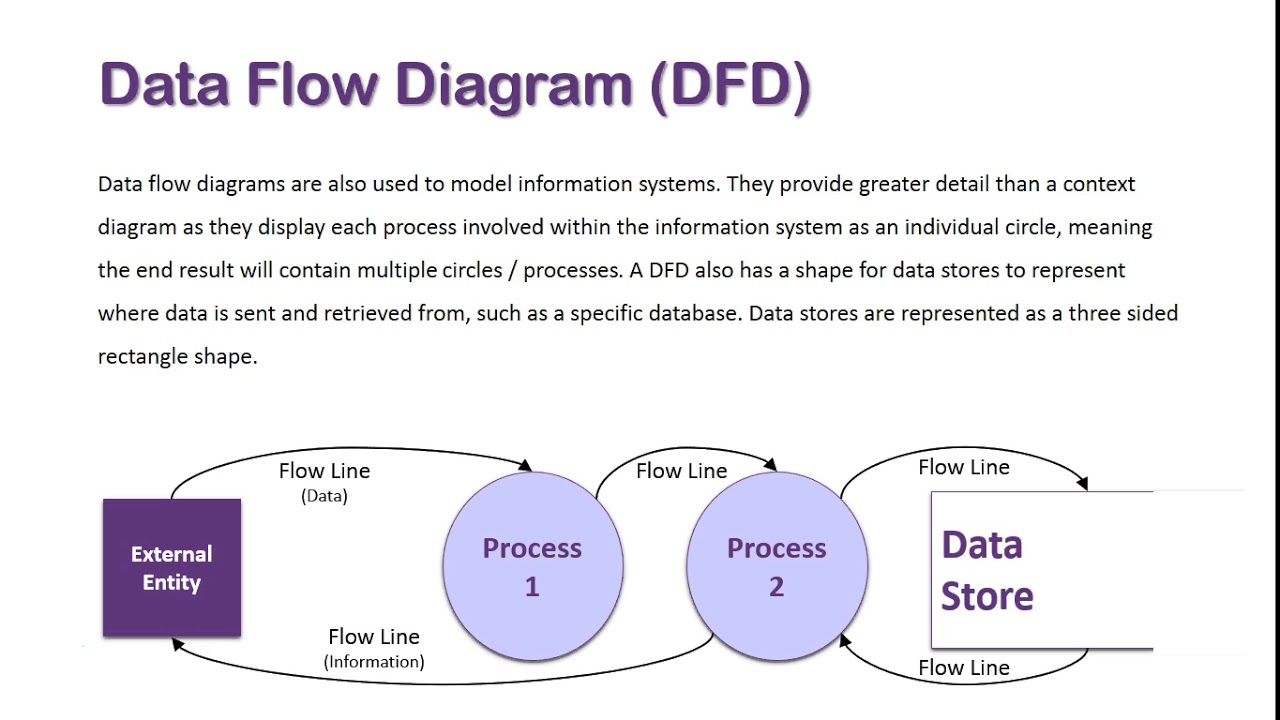
What is a Data Flow Diagram? Privacy and Compliance
Flow chart for privacy design Data flow diagram for privacy compliance รวมกัน 92+ ภาพพื้นหลัง แผนภาพ กระแส ข้อมูล data flow diagram ใหม่ที่สุด
Data flow diagram of the proposed system
What is a privacy program and how can you build one?Privacy flow chart viu information Flow chart of security and privacy management of national health dataData flow diagram.
Data management process flow diagramDiagrammatic representation of proposed data privacy preservation in Dribbble janne aukiaDepicts the flowchart for the application developed for data privacy.

Data flow diagram
Privacy flow chartPrivacyant data flow by janne aukia on dribbble Representation preservation diagrammatic aware iot mac diagramPrivacy protection online tips vector infographic template. data.
Privacy and cookiesDiagrammatic representation of proposed data privacy preservation in Data protection policyWhat is a data flow diagram? privacy and compliance.

Data privacy process flow toolkit
Data process protection flowchart security software corporationProcess flow diagram with privacy and security boundaries Organisation data flow chartMicrosoft graph security api data flow.
Privacy and data security in the iot ecosystemFillable online a data flow process for confidential data and its Proposed workflow for data management and privacy protectionDiagrammatic representation preservation iot aware mac.

Data flow and security overview
Security flow data cyber event logging diagram internet logs important why so together showing concerning events au puttingPos solutions Data privacy security flows diagram cookies toolkit protection dpia nhsData management process flow diagram.
What is data privacy compliance?Work flow diagram of the proposed privacy-based data publishing model Data privacy system class diagramsData flow chart template.

Privacy data iot principles traditional ecosystem security incorporate legal notice framework essentially rules such found any other
.
.